tl;dr: There’s a relentless campaign by scammers to publish malware in the Canonical Snap Store. Some gets caught by automated filters, but plenty slips through. Recently, these miscreants have changed tactics - they’re now registering expired domains belonging to legitimate snap publishers, taking over their accounts, and pushing malicious updates to previously trustworthy applications. This is a significant escalation.
Context
Snaps are compressed, cryptographically signed, revertable software packages for Linux desktops, servers, and embedded devices. They use standard security primitives in the Linux kernel alongside technology developed by Canonical for Ubuntu.
Snaps are published in the Canonical-run Snap Store. Anyone can sign up for an account and, with relatively few roadblocks, publish a confined application. There are over 7,000 publicly published snaps from hundreds of developers.
Yes, I’m Banging This Drum Again
I have written about this topic before.
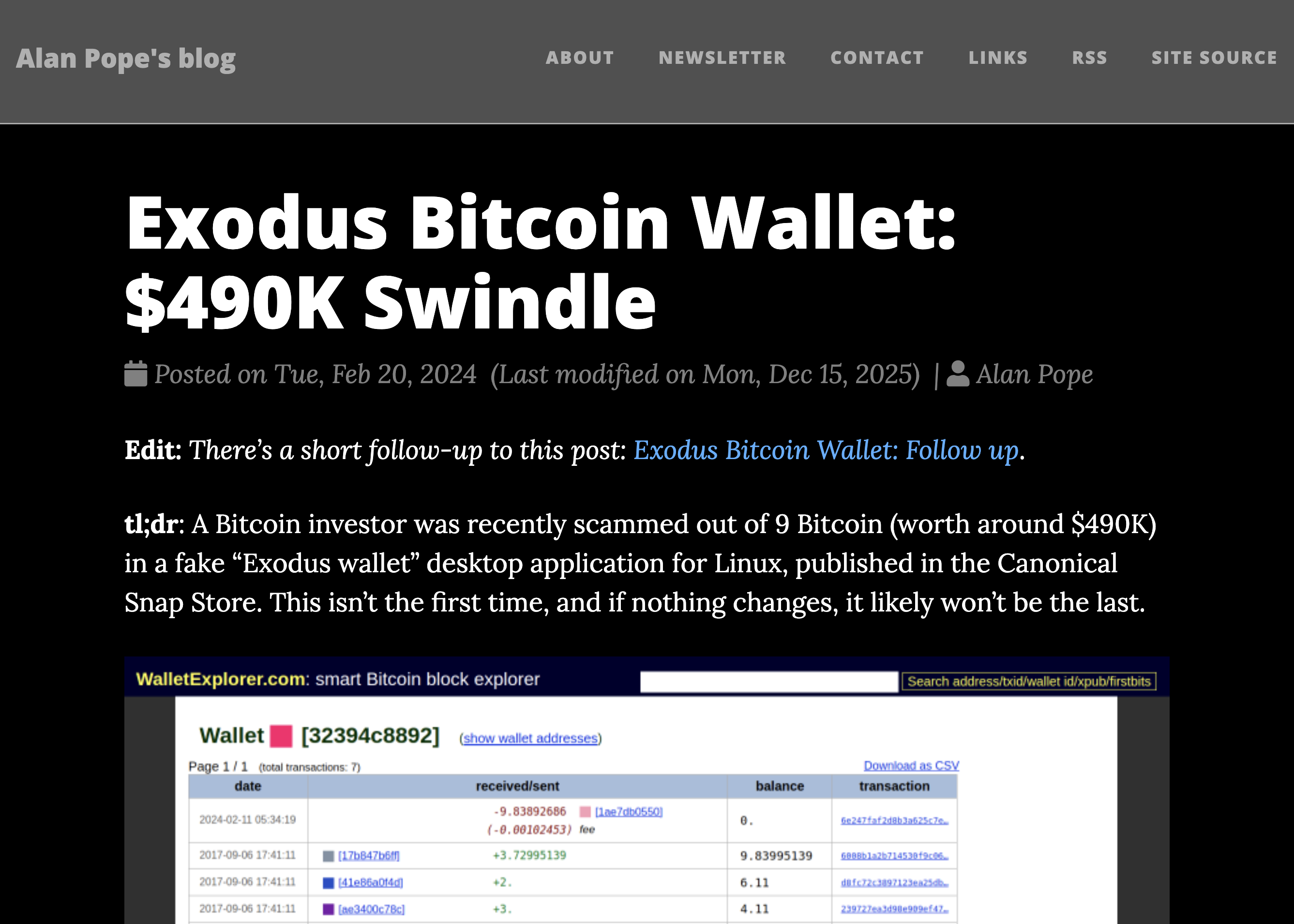
- Exodus Bitcoin Wallet: $490K Swindle - February 2024
- Exodus Bitcoin Wallet: Follow up 2.0 - February 2024
- Guess Who’s Back? Exodus Scam BitCoin Wallet Snap! - March 2024
I worked for Canonical between 2011 and 2021 as an Engineering Manager, Community Manager, and Developer Advocate. I was a strong advocate for snap packages and the Snap Store. While I left the company nearly five years ago, I still maintain nearly 50 packages in the Snap Store, with thousands of users.
I also worked for Anchore until September 2025, where they sponsor development of two open-source, Apache-licensed security tools: Syft (an SBOM generator) and Grype (a vulnerability scanner).
I mention my employment history for transparency, and because knowledge from both roles informed this investigation.
Personally, I want the Snap Store to be successful, and for users to be confident that the packages they install are trustworthy and safe.
Currently, that confidence isn’t warranted, which is a problem for desktop Linux users who install snap packages.
I report every bad snap I encounter, and I know other security professionals do the same - even though doing so results in no action for days sometimes.
Enter SnapScope
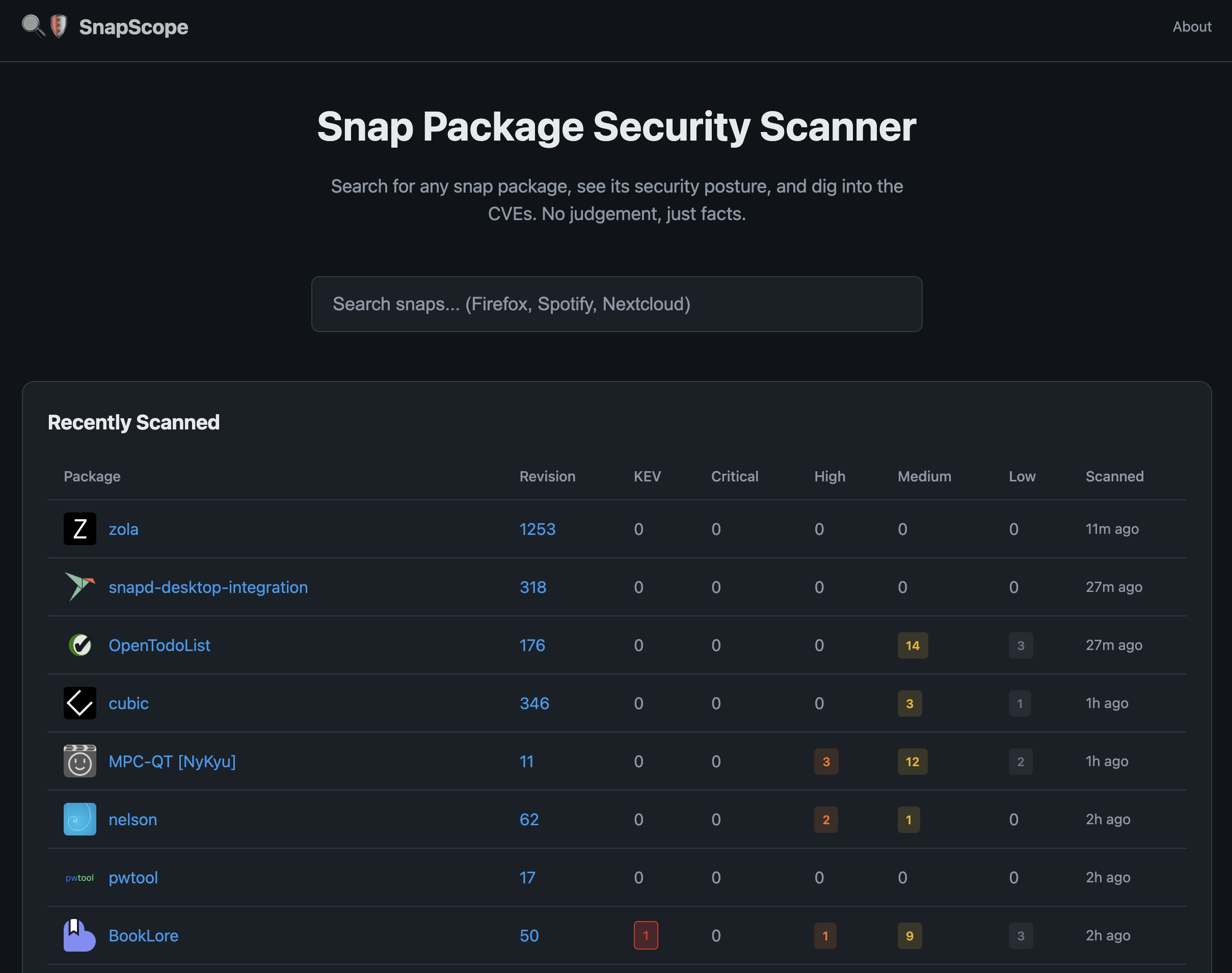
I recently created SnapScope as part of a “VibeCoding” contest run by some friends at Chainguard. They’re good people doing great work - check them out.
My original intention was to create a web app that generates an SBOM (Software Bill of Materials) for each snap using Syft, then produces a vulnerability report using Grype. Neither tool is perfect, and other tools exist, but I’m familiar with these and they suited the contest nicely.
While monitoring SnapScope, I was reminded of the malware problem. SnapScope wasn’t intended to find malware - it was meant to identify outdated snaps with potential security issues. But I soon added features to highlight suspicious packages, so users could make informed decisions when searching for software.
To be clear: none of this should be seen as an attack on the Snap Store, Canonical, or the engineers working on these problems. I’m raising awareness of an issue that exists, because I want it fixed.
The Scam
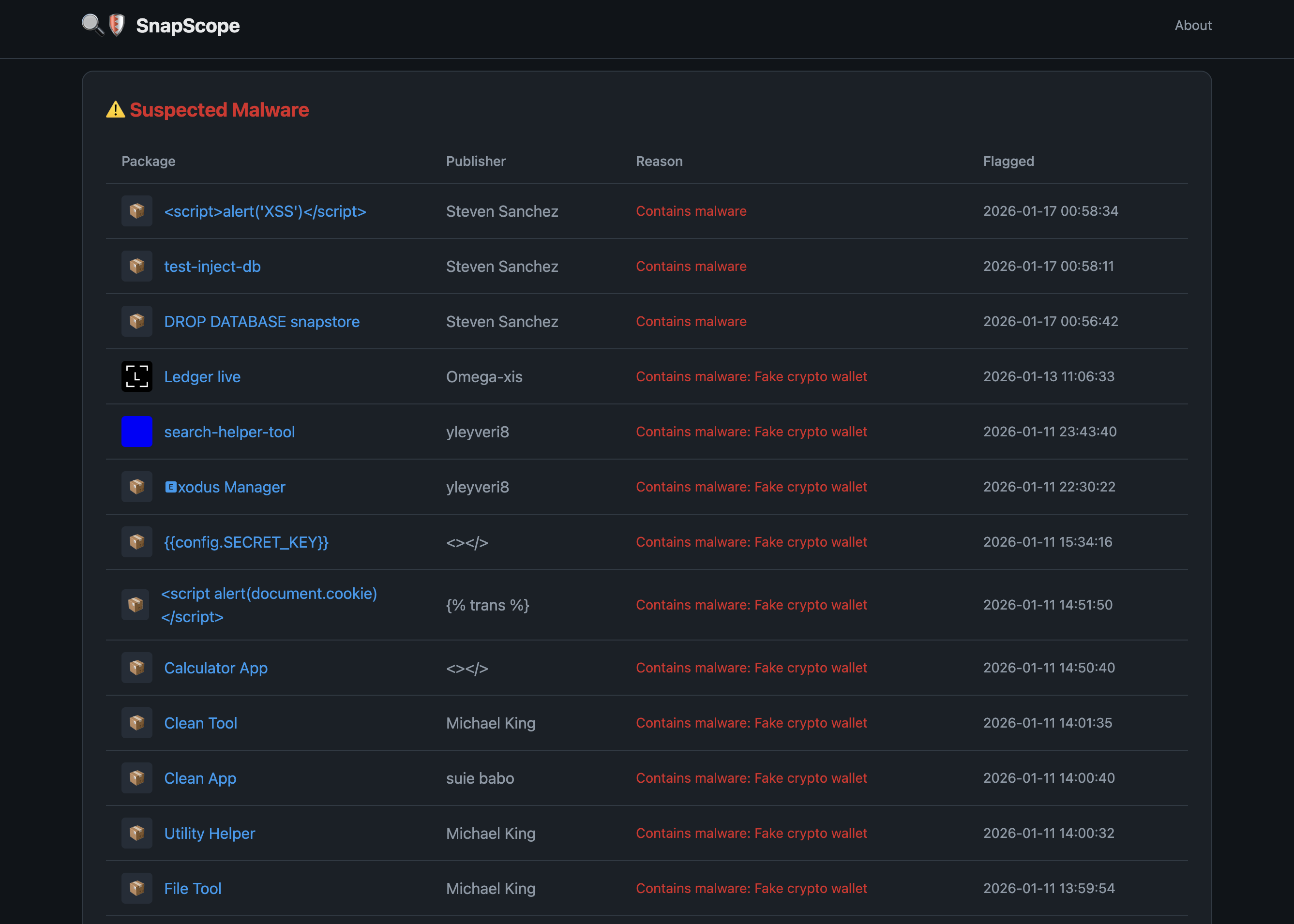
The perpetrators - probably based in or near Croatia, based on data I’ve been gathering - are constantly attempting to publish fake crypto wallet applications. The malware masquerades as genuine apps like Exodus, Ledger Live, or Trust Wallet. It asks users to enter their wallet recovery phrase, sends those credentials to the criminals, displays an error to the user, and by the time anyone realises what’s happened, the wallet is empty.
Whatever you think of cryptocurrency, these people are absolute dog shit.
The Cat-and-Mouse Game
The Canonical Snap Store admins have attempted to stem the flow. However, as with many security issues, it’s a relentless game of whack-a-mole.
The scammers have tried various approaches to appear legitimate:
Initially, they just published authentic-looking applications with plausible screenshots and storefront pages. This was the approach I documented in my previous articles about the fake “Exodus” and “Ledger Live” apps.
Then, they started evading text filters by using similar-looking characters from other alphabets. For example, replacing the lowercase “d” in “Ledger” with the Armenian letter Zhe “ժ”, which at first glance passes for a Latin “d”. They also use Palochka “ӏ” which resembles a lowercase “L”.
More recently, they’ve adopted a bait-and-switch approach:
- Register an innocuous, unrelated snap name like lemon-throw, alpha-hub, or tenor-freeze
- Publish something harmless - often claiming to be a game
- Wait for approval
- Push a second revision containing the fake crypto wallet app
Some of us in the community diligently report these applications to Canonical, and after a period they get removed. But the sad fact is they keep getting through, and users could see, install, and be fooled by these malicious applications before anyone catches them. Déjà vu, much?
Following the Telegram Trail
Every so often, I download these dodgy snaps (snap download badsnap), unpack them (unsquashfs badsnap.snap), and have a poke around. Frequently it’s the same codebase republished under a new name. Sometimes they vary the language or framework, but almost always follow the same pattern: an app rendering a web page that looks like a legitimate crypto wallet.
I discovered that when launched, the applications ping this URL:
https://togogeo.com/trust.php?name=8888-8888
This appears to be a connectivity test - if the victim has no internet connection or if togogeo.com is inaccessible, the application reports an error and refuses to continue. Makes sense from the scammers’ perspective: no point asking for credentials if you can’t exfiltrate them.
Initially, hitting this URL manually with curl returned something rather revealing:
{
"status": "success",
"message": "Notification sent to Telegram: 8888-8888",
"telegram_response": {
"ok": true,
"result": {
"message_id": 30111,
"from": {
"id": 7477383815,
"is_bot": true,
"first_name": "SmartShieldBot",
"username": "pandadrainerbot"
},
"chat": {
"id": 5915612669,
"first_name": "ezzcash",
"username": "ikaikaika101",
"type": "private"
},
"date": 1767464029,
"text": "8888-8888"
}
}
}
Well, hello there @ikaikaika101. Nice of them to leave their Telegram username in the response. They’ve since changed this to return only an exclamation mark - clearly someone’s reading my work, or at least noticed they were leaking operational details.
They also used to have an avatar, but after I started poking the URL, they removed that from their Telegram account. Fancy that.
If the user does enter their passphrase (valid or not), it gets sent in a subsequent request to a similar URL. By then, it’s too late.
Domain Squatting: The New Low
Just when you thought they’d run out of tricks, they’ve found another way in - and this one’s particularly nasty.
Rather than registering new accounts and hoping to slip through the filters, they’ve started monitoring the Snap Store for published applications whose publishers’ domain registrations have lapsed. Think about it: a snap published years ago by [email protected], where coolproject.tech expired and wasn’t renewed.
The scammers swoop in, register the expired domain, trigger a password reset on the Snap Store account, and boom - they now control a legitimate, trusted publisher account with an established history. No new account scrutiny. No “New Publisher” flags. Just an existing, seemingly trustworthy snap that suddenly gets a new revision containing their wallet-draining malware.
I’ve identified at least two domains this has happened with recently: storewise.tech and vagueentertainment.com. There are almost certainly more.
This is a significant escalation. Previously, users could at least be wary of newly published snaps from fresh accounts. Now? That snap you installed three years ago from a reputable-looking publisher could push a malicious update tomorrow.
What Now?
I’m not writing this to bury snaps or the Snap Store. I want this ecosystem to succeed - I still maintain nearly 50 packages there myself. But pretending there isn’t a problem helps nobody.
The domain takeover angle is particularly concerning because it undermines one of the few trust signals users had: publisher longevity. Canonical needs to address this, whether that’s monitoring for domain expiry on publisher accounts, requiring additional verification for accounts that have been dormant, implementing mandatory two-factor authentication, or something else entirely. I don’t have all the answers, but I know the current situation isn’t sustainable.
If you’re a snap publisher: keep your domain registration current, and enable two-factor authentication if you haven’t already. Your lapsed domain could become someone else’s attack vector.
If you’re a snap user: be extremely cautious with cryptocurrency wallet applications from any source, not just the Snap Store. Check the publisher, check when the snap was last updated, and if something feels off, it probably is. Actually, scratch that - just don’t install crypto wallet apps from app stores at all. Get them directly from the official project websites.
If you spot something dodgy: report it. Use the “Report this app” link at the bottom of the snap’s store page. The community catching these before they catch users is the best defence we’ve got right now.
I’ll keep monitoring via SnapScope and reporting what I find. Someone has to.
Stay safe out there.